Information security policy
Information Security Policy
To safeguard the confidentiality, integrity, and availability of its information assets, Jebsee has established a comprehensive information security management framework. This framework supports the continuous operation of business systems, ensures compliance with applicable laws and regulations, and protects information assets against intentional or accidental internal and external threats.
Policy Principles
- Strengthen personnel knowledge and information security competencies
- Prevent data leakage and unauthorized access
- Implement effective daily system maintenance and monitoring
- Ensure the availability and reliability of critical services
Information Security Objectives
- Provide regular information security education and training to enhance employee awareness and clarify security responsibilities
- Protect business and operational information from unauthorized access, alteration, or disclosure, ensuring data accuracy and integrity
- Conduct periodic internal and external audits to verify the effective implementation of information security controls
- Maintain defined availability levels for critical business systems to support stable and continuous operations
ISM Information Security Management Committee
In 2024, Jebsee established the Information Security Management Committee (ISMC) to strengthen information security governance across the organization. The Committee is chaired by the General Manager, with the Head of the Digital Transformation Department appointed as the Information Security Officer (ISO) and serving as the Committee Convener.
The ISMC is responsible for overseeing the implementation of information security policies, coordinating resource allocation, and ensuring the effective operation of the information security management system. The Committee regularly reports information security performance and risk status to the Chairman to support informed oversight and continuous improvement.
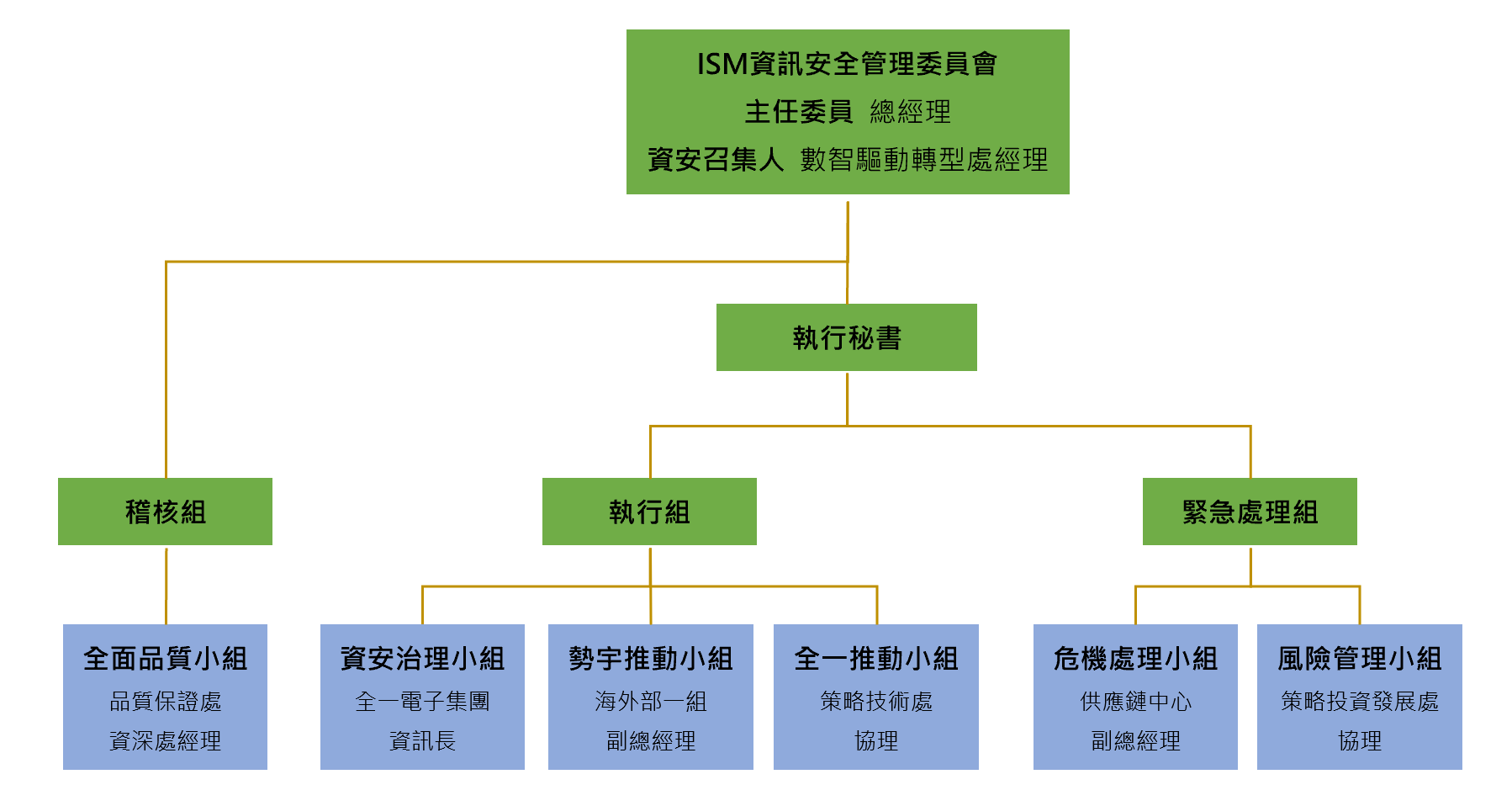
Information Security Governance Structure
Jebsee has established a clear and structured information security governance framework to ensure effective oversight, coordination, and incident response across the organization. Under the direction of the Information Security Management Committee, dedicated functional teams are responsible for policy execution, audit oversight, operational implementation, and incident response. This structure ensures that information security initiatives are consistently implemented, monitored, and improved across all business units and manufacturing sites.
Key Governance Functions
- Policy & Coordination
Oversees the implementation of information security policies, coordinates cross-functional execution, and monitors overall security status. - Audit & Compliance
Conducts regular internal audits to verify the effectiveness of information security controls and ensure compliance with applicable standards and requirements. - Execution & Implementation
Plans and executes information security operations, establishes management standards, and supports certification and compliance initiatives across manufacturing sites, including TISAX requirements where applicable. - Incident & Risk Management
Manages information security incidents and emergency response, coordinates resource allocation during critical events, and performs risk assessments to identify and protect critical information assets.
Information Security Management Framework
Jebsee operates a structured information security management framework covering the full lifecycle of information protection, from asset identification and risk management to operational control and continuous improvement.
The framework includes:
- Asset & Risk Management
Identification, classification, and risk assessment of information assets to ensure appropriate protection. - People & Access Control
Information security awareness training, role-based access control, and personnel security management. - Operational & Physical Security
Secure operation of information systems, physical security controls, and communication management. - System Development & Third-Party Management
Secure system development, maintenance processes, and oversight of outsourced service providers. - Incident Response & Business Continuity
Incident management, operational resilience, and continuous operation planning. - Audit, Monitoring & Continuous Improvement
Regular audits, performance measurement, corrective actions, and ongoing enhancement of security controls.
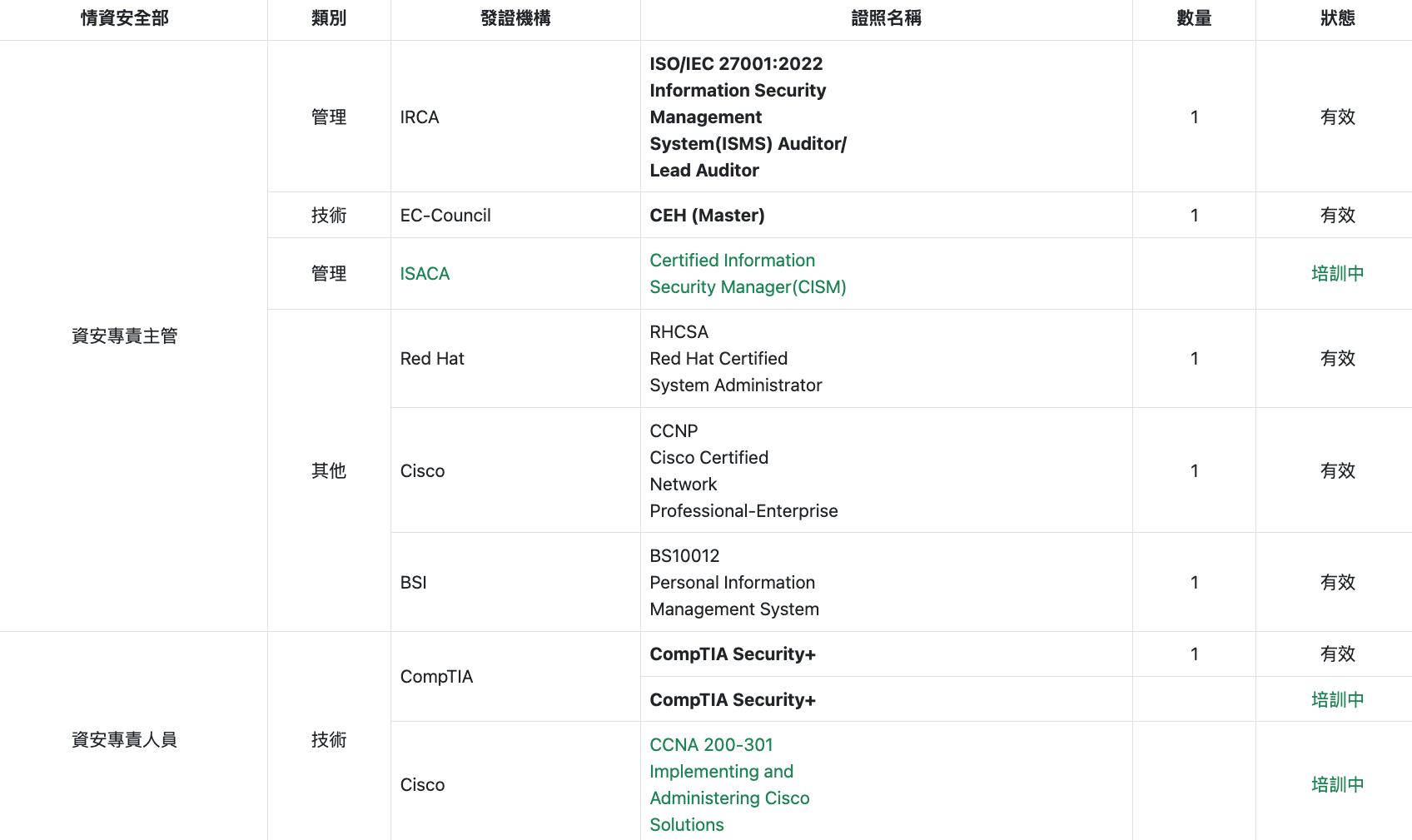
Information security seminars/professional training courses
| Study Dates | Organizer | Course Name | Continuing education hours | |
|---|---|---|---|---|
| Cybersecurity Manager | 2025/06/27 | CIO Taiwan | 2025 Manufacturing CIO Forum, Kaohsiung | 3 |
| Cybersecurity Manager | 2025/08/22 | CISO Cybersecurity Academy | 2025 High-Tech Cybersecurity Forum, Hsinchu | 6 |
| Cybersecurity specialist | 2025/08/27 ~ 2025/08/28 | SGS Taiwan Inspection Technology | ISO/IEC 27001:2022 Information Security Management System (LA Version) | 16 |
| Cybersecurity personnel | 2025/04/15 ~ 2025/04/17 | iThome Electric Week Cultural Project | 2025 Taiwan Cybersecurity Conference | 7 |
| Information personnel | 2025/02/11 ~ 2025/09/26 | Hezhen Technology Services | Introduction to TISAX Standards, Asset Inventory and Risk Assessment, Internal Audit | 3 |
| Information personnel | 2025/03/18 ~ 2024/08/12 | Hezhen Technology Services | Cybersecurity General Education Course (per quarter) | 3 |
Information security seminars/professional training courses